Presentations
Speakers: Xuan Xing, Eugene Rodionov
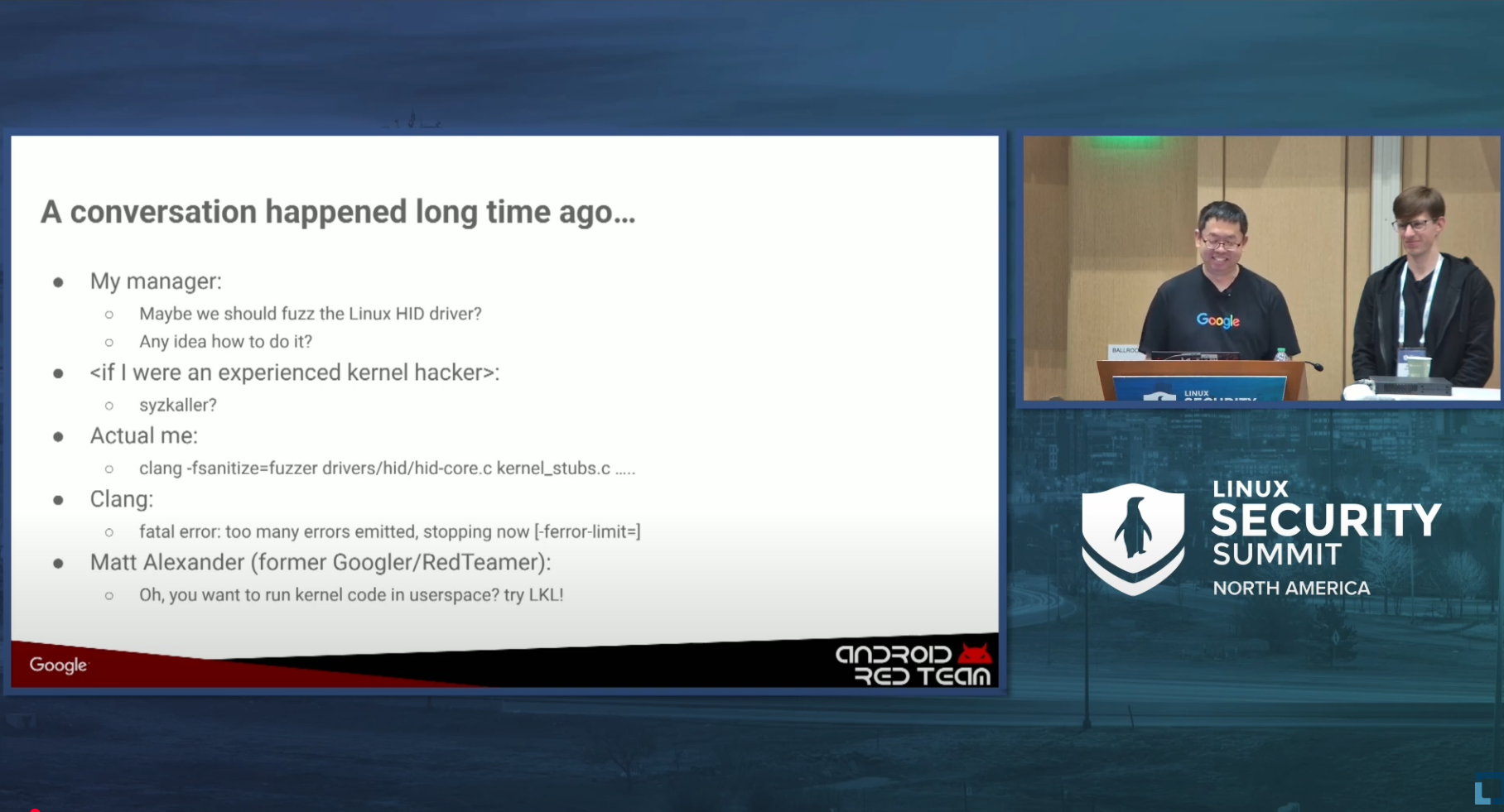
Linux kernel is one of the key attack surfaces for Android, and fuzzing is a very important approach for vulnerability discovery in this area. While looking into different kernel areas, Android Red Team approaches them with a novel approach, allowing Linux kernel fuzzing from userspace using Linux Kernel Library, a.k.a LKL.
This work was presented at the following two conferences:
Speakers: Jeong Wook Oh, Rishika Hooda, Xuan Xing
Bluetooth has always been a risky area due to its spec complexity and its remote access factor. This talk covers the joint effort between Android Red Team and Android Bluetooth team on securing the AOSP Bluetooth stack.
Speakers: Dominik Maier
Our team member Dominik Maier talks about LibAFL, the state-of-the-art fuzzing library by the AFLplusplus project, and explores its more advanced features. As a LibAFL maintainer, he will walk through the tricks and techniques that can help finding (or preventing) vulnerabilities faster, even within complex binary-only targets.
Speakers: Xiling Gong, Xuan Xing, Eugene Rodionov
The security researcher Xiling Gong from Android Red Team looked into Qualcomm Adreno GPU driver, discovered several high severity issues, and exploited one of them to gain root privilege from untrusted apps.
Speakers: Eugene Rodionov, Zi Fan Tan, Gulshan Singh
This presentation covers results of Android Red Team binder engagement and provides technical details on how the team reviewed the binder driver for security vulnerabilities, and exploited one of the discovered issues to gain local root privilege from untrusted apps.
The same content was also presented at GeekCon 2024, Shanghai
Speakers: Farzan Karimi, Xuan Xing, Xiling Gong, Eugene Rodionov
Android Red Team securing Pixel baseband by offensive research. This talk provides technical details of the identified issues in 2G and ASN.1 attack surface including demonstration of over-the-air exploit leading to arbitrary code execution on the communication processor (aka modem).
Speakers: Eugene Rodionov, Will Deacon
Red Team methodologies used to secure attack surface on the pKVM hypervisor. This talk covers our virtio fuzzing approach and future work to help improve fuzzing of virtualized interfaces.
Speakers: Farzan Karimi, Xuan Xing, Eugene Rodionov, Christopher Cole
Android Red Team talks about how we helped on securing the Pixel 6 before launch, focusing on the perspective of the Android Red Team. The team demonstrates how various attack techniques were used to identify opportunities for privileged code execution in critical components. This session covers the first end-to-end proof of concept on the Titan M2 chip, as well as Android Bootloader (ABL) with full persistence resulting in a bypass of hardware key attestation.